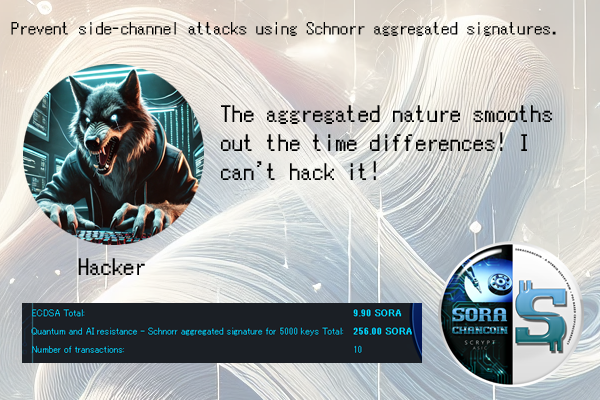
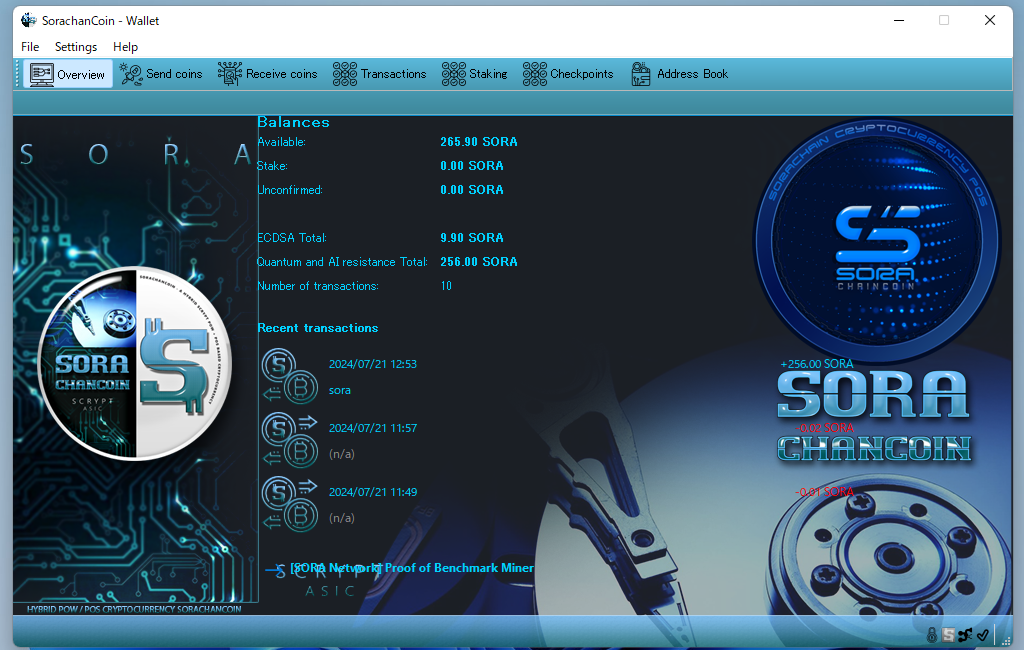
When private keys are aggregated, it becomes troublesome for hackers. This is because the differences in processing times are smoothed out.
From the hacker’s perspective, side-channel attacks on blockchain private keys seem to offer a low-risk, extremely high-reward opportunity. Normally, they would be required to make sophisticated and high-risk choices, such as taking control of the system. However, with side-channel attacks on private keys, they only need to hack a small piece of information related to the private keys, without attacking the system itself. In fact, if their intent is monetary gain, they wouldn’t do something that would leave a trail. After hacking, they can process it using their synchronized blockchain, so there’s no need to use someone else’s system for post-hack processing.